Hijacked Device
A hijacked device is an electronic gadget, such as a smartphone, computer, or IoT device, that has been taken over by unauthorized users or malware. This unauthorized control allows attackers to manipulate the device’s functions, access sensitive information, or use it for malicious activities without the owner’s consent.
What is Hijacked Device?
Understanding hijacked devices is critical for enterprise risk mitigation and operational continuity. A hijacked device—smartphone, computer, or IoT endpoint—has been commandeered by unauthorized actors or malware, enabling them to alter functions, exfiltrate sensitive data, and conscript assets for malicious campaigns without consent. For B2B environments, these compromises escalate lateral movement, disrupt workflows, and inflate compliance exposure. Proactive detection, segmentation, and zero-trust enforcement reduce blast radius, while continuous monitoring, firmware hygiene, and rapid incident response restore resilience. Educating employees on anomalous behaviors and enforcing least-privilege access further curtail attack surfaces, safeguarding partners, customers, and revenue from cascading, reputation-damaging security incidents globally.
Example
Promote a cybersecurity app by describing a scenario where a hacker hijacks a smartphone to steal personal data, then show how your app detects and blocks such unauthorized access to protect users.

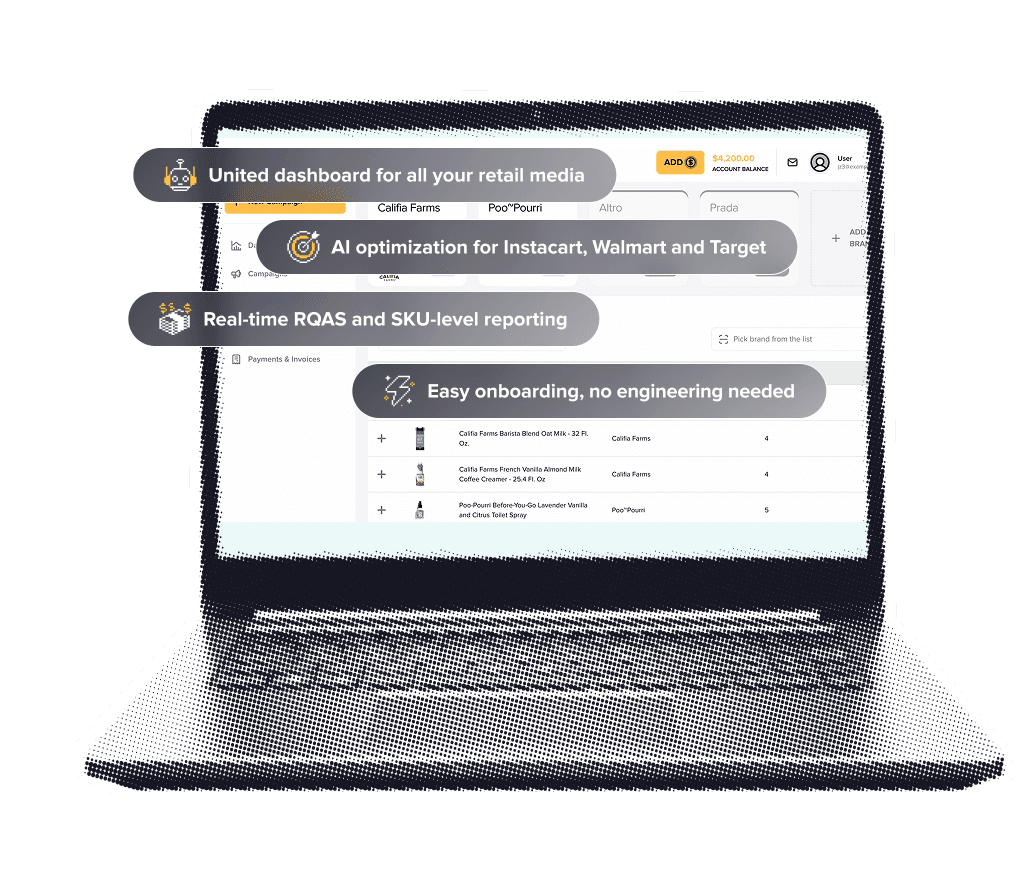
RMIQ helps brands mitigate the business impact of hijacked device activity by using its multi‑agent AI to detect anomalous signals across retail media networks and automatically safeguard budget, bids, and targeting in real time. By unifying Walmart, Instacart, Amazon, Sprouts, Thrive Market, Target, Uber, and more in a single platform, RMIQ correlates cross‑network patterns—sudden click spikes, erratic ROAS swings, or SKU‑level conversion drop‑offs—and orchestrates rapid containment through bid adjustments, negative targeting, budget reallocation, and A/B test gating without manual intervention. When device hijacking distorts traffic quality, autonomous agents throttle spend on affected placements, exclude compromised inventory, shift budget to proven segments, and refine keyword and SKU strategies to preserve ROAS, with reported performance lift averaging 50% and up to five dollars returned for every dollar invested.
Coverage across more than twenty retail media platforms, reaching up to 85% of the U.S. retail audience, ensures that detection and mitigation are applied consistently wherever risk emerges, while the unified interface consolidates dashboards, reporting, and workflows so your team can investigate issues quickly without juggling multiple log‑ins. Real‑time bidding, cross‑network learning, and SKU‑level insights enable precise, data‑driven decisions that minimize waste and keep campaigns on plan, even during short‑lived hijacking incidents. For program owners, the result is resilient execution: faster incident response, reduced financial exposure, and continuity of growth initiatives backed by adaptive strategies that learn and improve with each event.
Whether you manage a handful of products or thousands of SKUs, RMIQ scales policy controls and automated safeguards to match your operating model, pairs them with five‑minute onboarding, and supports your team with responsive service, delivering a next‑generation, AI‑driven approach to retail media risk management and optimization in a single, enterprise‑ready platform. This positions your brand to defend budgets proactively, protect revenue, and sustain performance even as threat landscapes evolve across marketplaces.
Coverage across more than twenty retail media platforms, reaching up to 85% of the U.S. retail audience, ensures that detection and mitigation are applied consistently wherever risk emerges, while the unified interface consolidates dashboards, reporting, and workflows so your team can investigate issues quickly without juggling multiple log‑ins. Real‑time bidding, cross‑network learning, and SKU‑level insights enable precise, data‑driven decisions that minimize waste and keep campaigns on plan, even during short‑lived hijacking incidents. For program owners, the result is resilient execution: faster incident response, reduced financial exposure, and continuity of growth initiatives backed by adaptive strategies that learn and improve with each event.
Whether you manage a handful of products or thousands of SKUs, RMIQ scales policy controls and automated safeguards to match your operating model, pairs them with five‑minute onboarding, and supports your team with responsive service, delivering a next‑generation, AI‑driven approach to retail media risk management and optimization in a single, enterprise‑ready platform. This positions your brand to defend budgets proactively, protect revenue, and sustain performance even as threat landscapes evolve across marketplaces.
Skills and tools for Hijacked Device
Skills needed include knowledge of networking, operating systems, and cybersecurity vulnerabilities. Tools commonly used are malware, remote access trojans (RATs), phishing kits, and exploitation frameworks like Metasploit. Attackers also use social engineering to gain access.
Our Current Partners
We are already helping leading retailers and platforms grow their retail media businesses, including:




Drop your email
and we’ll show you how to double your retail media ROAS – no strings attached